Learn advanced Skills from THECYBERHOST Courses.






Ethical hacking courses continue to be relevant and important in 2024 due to the increasing reliance on technology and the ongoing threats posed by cybercrime. .

Ethical Hacking course enhances cybersecurity skills and knowledge for protecting systems and networks against 'cyber threats.
The Cyber Security market is projected to expand substantially by 2025 due to rising threats and increased emphasis on digital security. This growth will lead to a surge in job opportunities for cybersecurity professionals in various roles.. Join THECYBERHOST Ethical Hacking Course Course today!
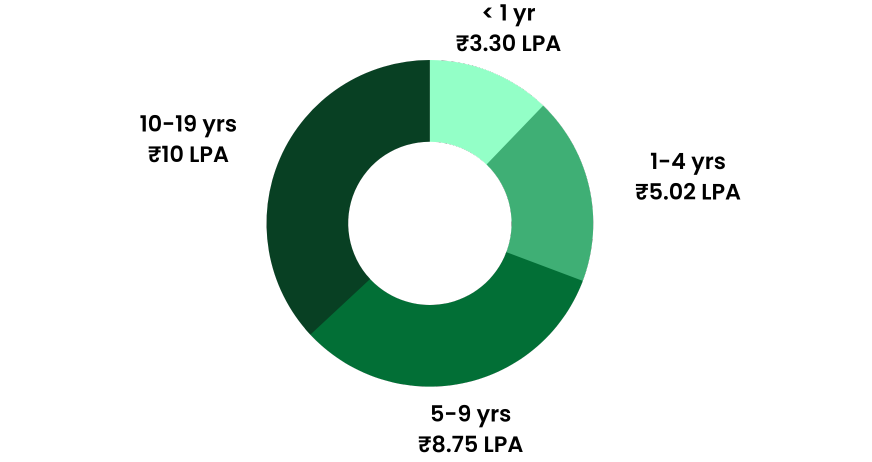
Annual Salary

Hiring Companies
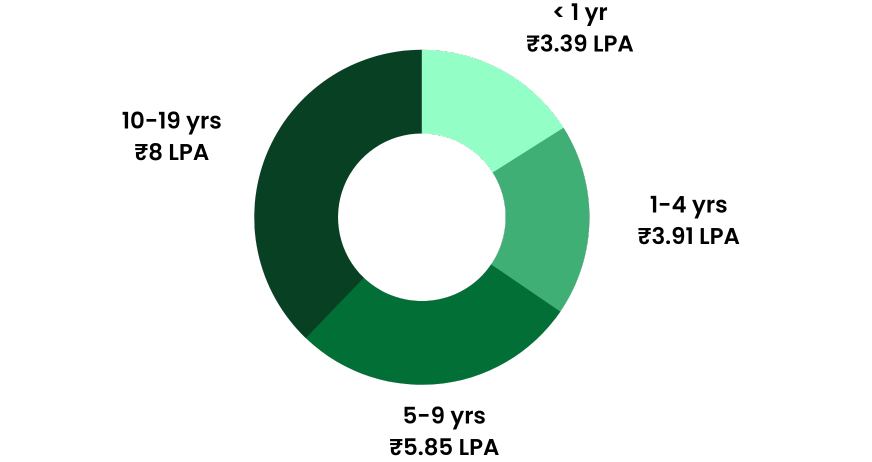
Annual Salary

Hiring Companies
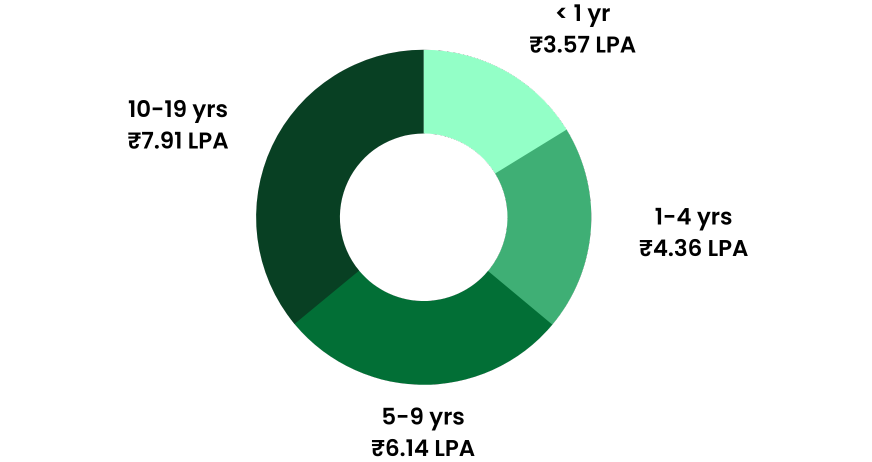
Annual Salary

Hiring Companies
Elevate your Cyber Security skills with Advanced training and unlock new career opportunities.
We are happy to help you 24/7
Instructor-led Ethical Hacking Course Live Online Training Schedule

During the training, you will gain proficiency in a wide range of essential skills and cutting-edge tools in the field of cybersecurity.
Linux Fundamentals
Android Hacking
Vulnerability Analysis
Password Cracking
System Hacking
Metasploit Framework
Web App Penetration Testing
Cryptography
Wifi Penetration testing
IoT Hacking
Unlock the full potential of your data with Excel! Its powerful and intuitive tools will leave you amazed at how much you can achieve.
Nmap
Metasploit
Ettercap/Bettercap
Wireshark
Burpsuite
Nessus
John The Ripper
Sqlmap
Hydra
More tools Will Be Covered





















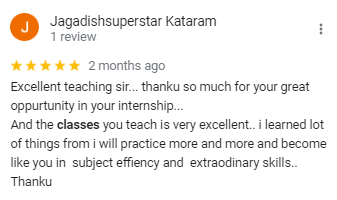
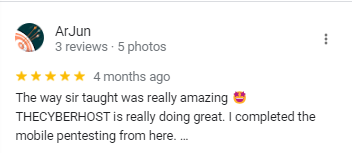
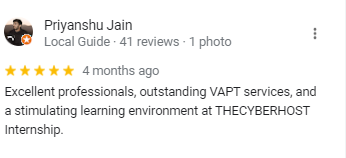
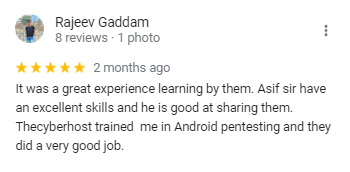
We Are Trusted & Rated.